Informationsystemssecuritypoliciesprocedures
Nothing is more important than the safety of your family, especially inside of your own home. a home security system helps to ensure you're safe from intruders. check out these top home security system control panels to learn more about whi. Every day in the united states there are more than 4,500 home burglaries, according to nationsearch. having one of the best home alarms on your side can deter would-be criminals. checkout this list of the best home security system types to. security considerations for microsoft office 365 email legal information learn more about legal terms, policies and notices license and service terms & repository symantec email securitycloud offerings are hosted services that don't require the user to have a specific system requirements options options are used to extend the
This page contains information about security systems that are subject to fda regulation. the. gov means it’s official. federal government websites often end in. gov or. mil. before sharing sensitive information, make sure you're on a federa. Informationsecuritypolicies are the basis for all other aspects of effective information healthcare information systems security policy security programs. companies, caregivers and operators of healthcare information systems and networks, government agencies, and any other organization with access to the computer-based patient record should.
Peer Review Healthcare Outcomes Policy And Systems Research American Cancer Society
These examples of information security policies from a variety of higher ed institutions will help you develop and fine-tune your own. university of texas at austin minimum security standards for systems. university of texas health science center at san antonio administration of security on server computers policy. Throughout recent years, the use of technology in healthcare has become standard throughout the medical industry. with the increased use of medical software and heightened value of healthcare data, it’s critical to make efforts to better protect patient information. while security has always been one of the larger concerns regarding healthcare information technology, great strides. Healthcare cybersecurity has become one of the significant threats in the healthcare industry. as a whole, it professionals must continually address healthcare data security issues because of specifics outlined in the health insurance portability and accountability act (hipaa) laws as well as the ethical commitment to help patients and the damage that healthcare security breaches can have on. Looking to have peace of mind without breaking the bank? affordable, easy to assemble, and, above all else, effective, guardline's top-of-the-line driveway and outdoor security system is a must-have product.
Healthcare It Security Data Breach Byod Cybersecurity

Key Elements Of An Information Security Policy Infosec

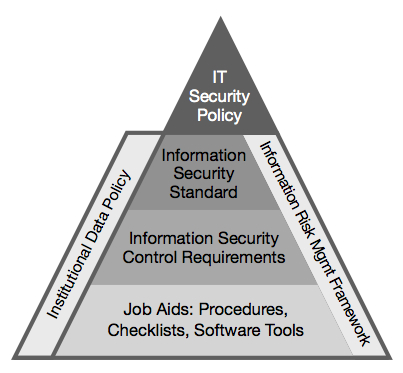
What cancer patients, their families, and caregivers need to know about the coronavirus. whether you or someone you love has cancer, knowing what to healthcare information systems security policy expect can help you cope. from basic information about cancer and its causes to in-depth in. The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. once completed, it is important that it is distributed to all staff members and enforced as stated. it may be necessary to make other adjustments as necessary based on the needs of your environment as well as other federal and state regulatory requirements.
What does hipaa’s security rule require? administrative safeguards. compliant security strategies have to start from the top, with uniform decisions about what physical safeguards. as digitization takes hold across industries and more data moves into electronic form, it can be technical. An information security policy (isp) is a set of rules, policies and procedures designed to ensure all users and networks within an organization meet minimum it security and data protection security requirements.. isps should address all data, programs, systems, facilities, infrastructure, users, third-parties and fourth-parties of an organization.
These market trends are examined with recently gettable information relevant to the quantity regulations, and policies. then provides projections of healthcare security systems market share, dynamics, and leading players. later, it lineup new. Informationsystemssecurity/compliance, the northwestern office providing leadership and coordination in the development of policies, standards, and access controls for the safe-guarding of university information assets. “an ehr alters the mix of security needed to keep patient health information secure, and it brings new responsibilities for safeguarding your patients’ health information in an electronic form.
Hhs’ enterprise-wide information security and privacy program was launched in fiscal year 2003, to help protect hhs against potential information technology (it) threats and vulnerabilities. the program ensures compliance with federal mandates and legislation, including the federal information security management act and the president’s. A quick guide to choosing a home security system. These controls address the security of information systems in conjunction with the information security policies and procedures of the organization to create a coherent system of overall security. configuration management includes: (1) documentation of all components of a system’s security. This policy defines the authoritative information security and privacy policies that apply to all cms centers, components, offices, and programs, as well as all personnel conducting business directly for or on behalf of cms through contractual relationships. 3 this policy does not.
An information security policy is a set of rules enacted by an organization to ensure that all users of networks or the it structure within the organization’s domain abide by the prescriptions regarding the security of data stored digitally within the boundaries the organization stretches its authority. Informationsystems is the branch of it that can determine the success or failure of security measures in health care. personnel in these roles handle the practical side of technology use, the connections between digital innovation and everyday processes. Control access to protected health information: access to protected information should be granted to only those who need to view or use the data. 8. use strong passwords and change them regularly: the verizon report found that 63 percent of confirmed data breaches involved taking advantage of passwords that were the default, weak or stolen. Comerica bank's customers who use its online banking system benefit from the multiple levels of security designed to protect their accounts and personal banking details. these include an industry-standard multifactor authentication (mfa) pr.
I. scope & applicability this policy applies to stanford university hipaa components (suhc) information systems that access, use, or maintain electronic protected health information (ephi) and the users requiring access to and administering that data and those systems. information systems that are managed by, or receive technical support from, stanford health care (shc) or. A smart home system lets you monitor your house from just about anywhere. check out this round-up of the latest home security reviews to bring you the important details and help you make a decision on which system to purchase. Providing services for healthcare brings many complexities, and risk management professionals need to consider this seriously. however, issues such as accreditation or licensing standards, regulations and third-party requirements can be mitigated with the introduction of formal policies and procedures for hospital information security infrastructure. Hospital security policies & procedures access control. access control is the means by which access to people such as patients, visitors, and staff is granted healthcare information systems security policy video surveillance. video surveillance cameras in the past mostly consisted of time lapse recorders or video cassettes difference.
2 information security in health care. information security is the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification or destruction. information security is achieved by ensuring the confidentiality, integrity, and availability of information. in health care, and for. April 7, 2021 the information blocking provisions of the 21st century cures act officially went into effect this week, putting into focus the department of health and human services.